I’m a software engineer and I built a trebuchet during lockdown to launch Easter eggs at the neighbours’ gardens since we weren’t allowed to go see them.
- 8 Posts
- 130 Comments
Saddameurysm.
lol! There’s such a mix of people being genuinely helpful and people telling me the joke is past its sell-by date. But I hadn’t come across reflector before and will definitely give it a go—thanks :)
Thanks—I am running the zen kernel because I didn’t really understand the question during archinstall, and have added an AUR helper but still no lack of joy.
I’ll definitely give this a go—probably on Friday afternoon.
They are super cool and super territorial by all accounts. We were in a pop-up pub in a field and this guy kept coming to sit on our hands. I guess we were in his spot…

I do not like the sound of pickass finger nails. But it could explain the fungus.
It would also still be the speed of light. Always is, unless you specify ‘in a vacuum’ every time.
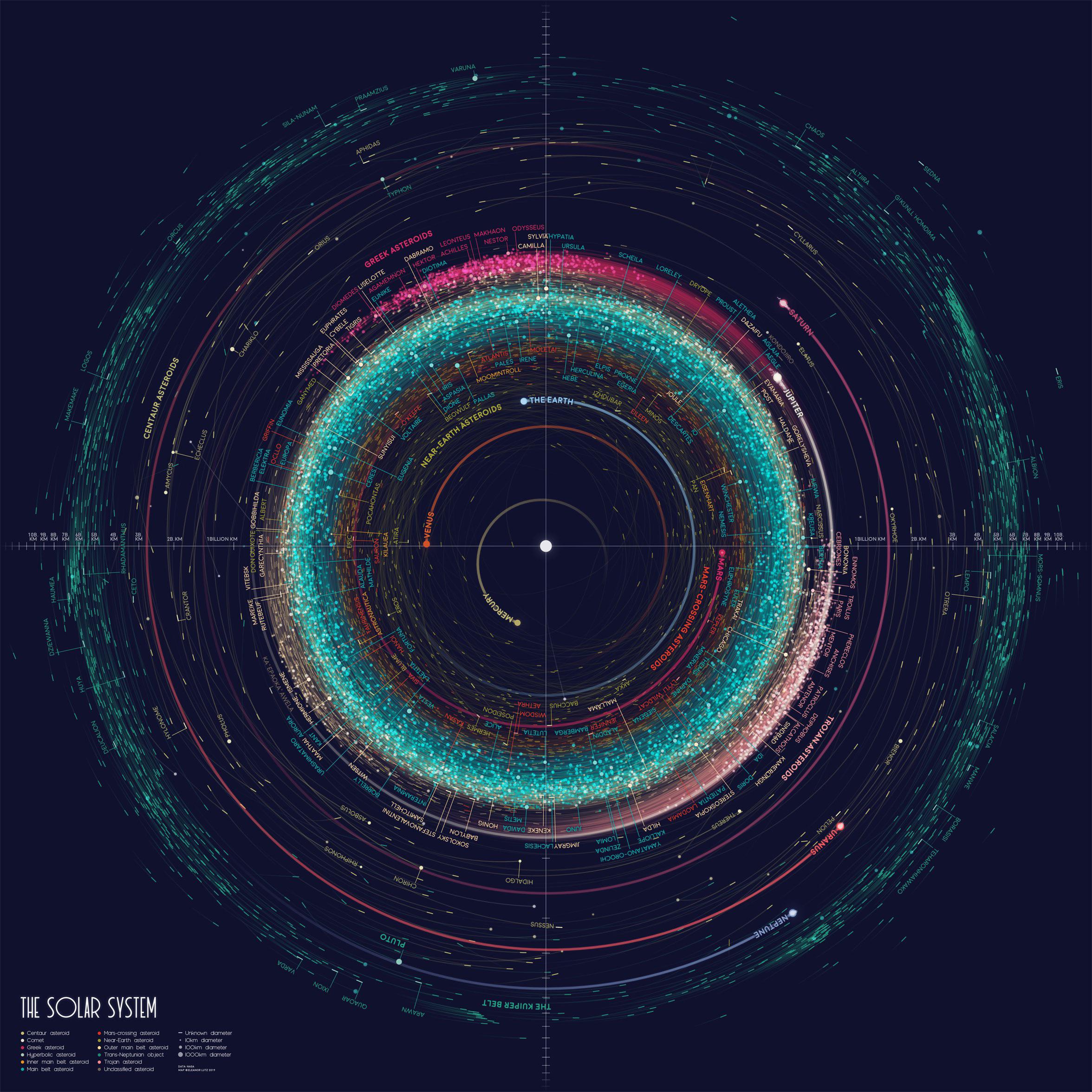
 1·4 months ago
1·4 months agoThat’s because the explanation is often a bit disingenuous. There’s practically no difference between “listening locally” and “constantly processing what you’re saying”. The device is constantly processing what you’re saying, simply to recognise the trigger word. That processing just isn’t shared off device until the trigger is detected. That’s the claim by the manufacturers, and so far it’s not been proved wrong (as mentioned elsewhere, plenty of people are trying). It’s hard to prove a negative but so far it seems not enough data is leaving to prove anything suspect.
I would put money on a team of people working for Amazon / Google to extract value from that processed speech data without actually sending that data off device. Things like aggregate conversation topic / sentiment, logging adverts heard on tv / radio for triangulation, etc. None of that would invalidate the “not constantly recording you” claim.
UK just went from announcement to election day in 6 weeks. But then, there wasn’t much point dragging it out any longer, was there Rishi ;)
Physicists:
This is just Occam’s razor again: a hypothetical particle that can’t interact with anything, and therefore can’t be detected, doesn’t exist.
Also Physicists: 85% of the universe’ mass is missing!!!
What happened to his ears?
Just use Reader view or whatever that’s called in your browser. I use Arctic for Lemmy on iOS and it has a ‘default to reader’ for opening links. Can’t remember the last time I saw a paywall. There’s one news site that doesn’t work but it’s pretty obvious straight away.
“All female shark tank” is my new band name.
This is a few years old, but I loved this one from London.


 15·6 months ago
15·6 months agoPartially. The summary isn’t quite in line with the detail:
Android is the only operating system that fully immunizes VPN apps from the attack because it doesn’t implement option 121. For all other OSes, there are no complete fixes. When apps run on Linux there’s a setting that minimizes the effects, but even then TunnelVision can be used to exploit a side channel that can be used to de-anonymize destination traffic and perform targeted denial-of-service attacks.
Just archive it and take up farming.











No, tiny bits of hidden software. It’s not a very efficient way of distributing code, but it was fun.